Let’s know about some Old Scams
In today’s digitization world, scammers are using a new technique to reach potential victims – sending an email and SMS, which comprises of links to common services like Alibaba cloud, Google Docs, Azure, and AWS. We have observed this sort of technique used for popular old scams like dating sites, tech support, and fake pharmacies that aim at stealing PII or blackmail victims. Today’s post is going to aware readers about some particular examples of the old scams & the strategy used by hackers to perform their scams and expand the causes why we are assuring it gain popularity.
Let’s See How Scammers Use Tech Support Trick
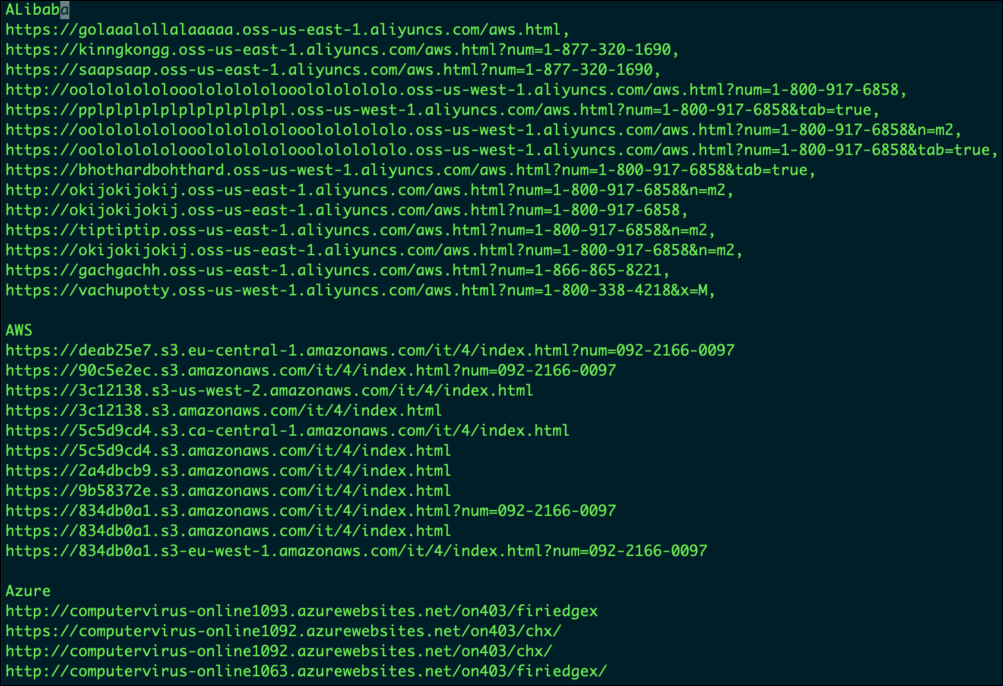
Tech support scams have been hosted in Alibaba, Azure, and AWS, with scammers rapidly shifting from one store to another, utilizing apparently arbitrary names. Some examples of static store URLs, which were hosting these old scams at the writing time are shown in the following figure.
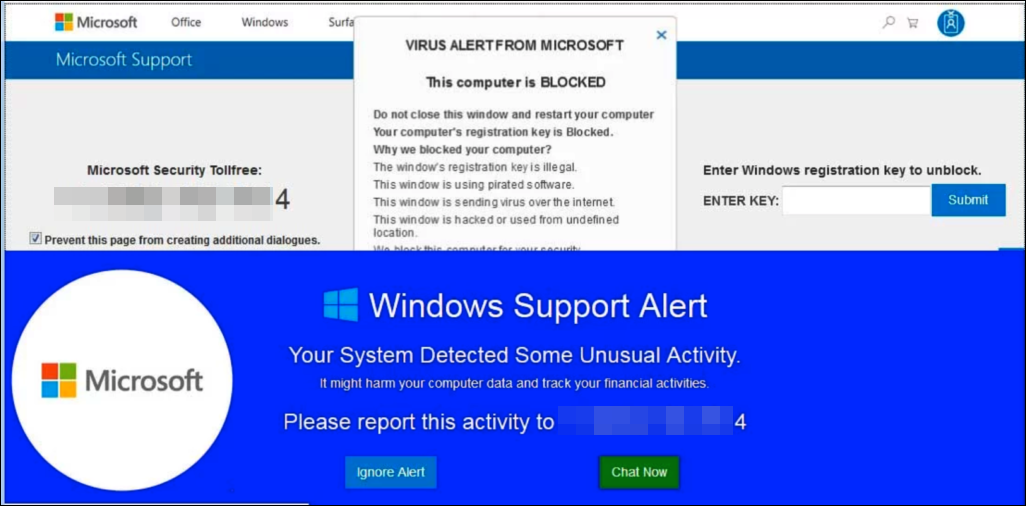
Another example depicts a page that was hosted at one of these links. In this scenario, a fraud Microsoft support web page convince the target to call for support. This work allows scammers to enforce social engineering tactics to fetch the credit card information. The simple way of quickly switching to another URL and poor hosting cost makes the services like AWS, Azure, and Alibaba a feasible target for scammers. Names in the object store can quickly get generated via a domain generation algorithm for making the terminating scams tough. Also, hackers can use compromised tenants or configure object stores in an incorrect manner to host the payloads.
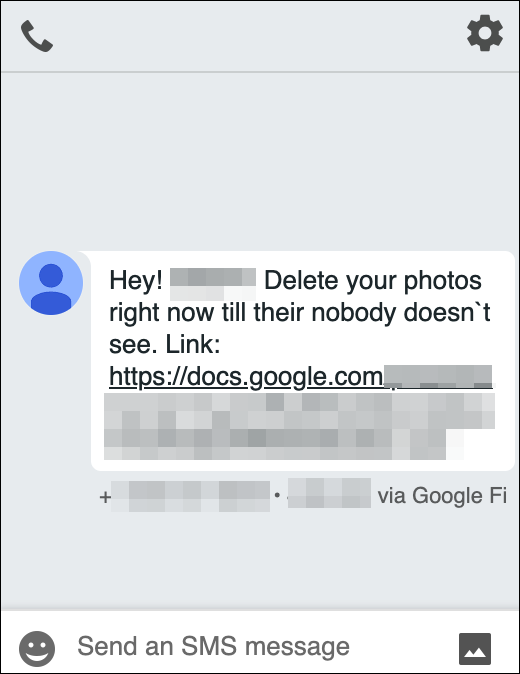
Its Time to Track the Use of G Docs in Smishing
In this example, you are going to notice that scammers are misusing G Docs for creating presentations and sharing them via smishing (SMS based phishing) and phishing. The presentation serves as a bait to secretively store the malicious link behind it.
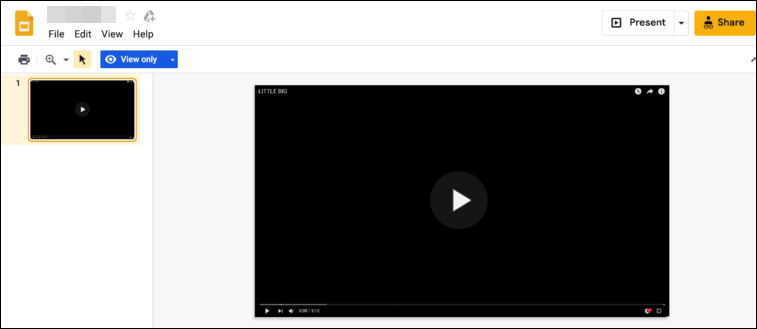
The links of Google Docs help hackers in bypassing spam filters that brief their use in phishing emails. The more curious part is the use of G Docs link in smishing. Google applications are already present in Android devices and are the most downloaded apps in iOS phones. This means that the link on smartphones are likely to get launch in its native application, where UX is seamless and clean, and the individual may have their low-security level. For example – the following figure shows the points of a hidden link to a website promising to provide adult content and dating services for free. It then greed users to tell their personal details like credit card information and email for age validation purpose.
Why Old Scams Are Still So Popular?
There are three main causes behind the increasing popularity of online services for known scams:
- Low and Dynamic Hosting – Use of online platforms like AWS, Google Drives, Azure, etc., enables attackers with the flexibility of moving here and there when their URLs are taken down. Open objects stores and the use of compromised tenants make the process more cost effective.
- Bypassing Traditional Data – Attaching the links with trusted services help hackers to bypass the traditional content filters like spam filters that may otherwise restrict the scams.
- Victims Get Easily Convinced – Services offered by AWS and Google Drive do not originate the same red flags as for the traditional malicious links. Besides this, the mobile data make it simpler for hackers to disguise malicious URLs like legitimate information.
How CloudCodes Provide the Protection?
CloudCodes CASB solution is programmed with such technologies that it has the capability of detecting the tech support scams. It restricts end users from opening untrusted, external Google Docs and hence, prevent them from unintentionally being getting saved or reshared.
Scammers using cloud computing services were inevitable. It provides them scale, helps them to ignore content filtering, and offers them a fresh channel where victims can have their guard down. While recently only being utilized for long-running scams aiming users, these approaches can also be utilized for targeted large enterprises who use services like Google Drive. In order to be safe from old scams and the trending one too, we have to immediately start educating people in our surroundings and companies should enforce Cyber security controls to secure themselves from the onslaught of hackers misusing cloud services

