Either it is the end of shopping season sale or festive sale, the time duration is lucrative to phishing attacks. It is so because spammers try to leverage the festive season for victimizing the online consumers. Retailer industries also face many challenges for meeting the demands of customers during the sale. A research laboratory has been tracking several campaigns in which phishing emails are designed for targeting the retail organization. During these campaigns, lab experts found that the message body is cleverly designed to tempt the warehouse managers. Not on managers but, other smaller organizations that render direct or indirect support to big retail businesses are also targeted. CloudCodes software detects these type of malicious file attachments and warns recipients, before opening it.
Role of Attack Vector – Phishing Attacks
An attack vector is a means through which a hacker acquires access to the targeted network server for causing malicious results. Attack vectors permit cloud attackers to diminish the system vulnerabilities, comprising the human components. In phishing attacks, this vector comes in the form of an email message with an attachment.
A weaponized Microsoft Word or Excel file is attached in the mail with macros inside it. In one of the industries, email attachments automatically get synchronized with cloud storage platforms through file collaboration settings. Online services might include third-party or SaaS applications. The filename of the attachment seems less suspicious due to which the recipient gets attracted to it for opening it. This entire scenario leads to arising in the effect of CloudPhishing fanout.
The pie chart shown in the following image depicts the popular business cloud software where CloudPhishing is challenging. Programs configured with the email platforms are more likely to be affected. For example – Google Drive and Microsoft OneDrive smoothly consolidate with their mail clients and therefore, documents also get synchronized with all users who are having permission to work with those synced drive folders.
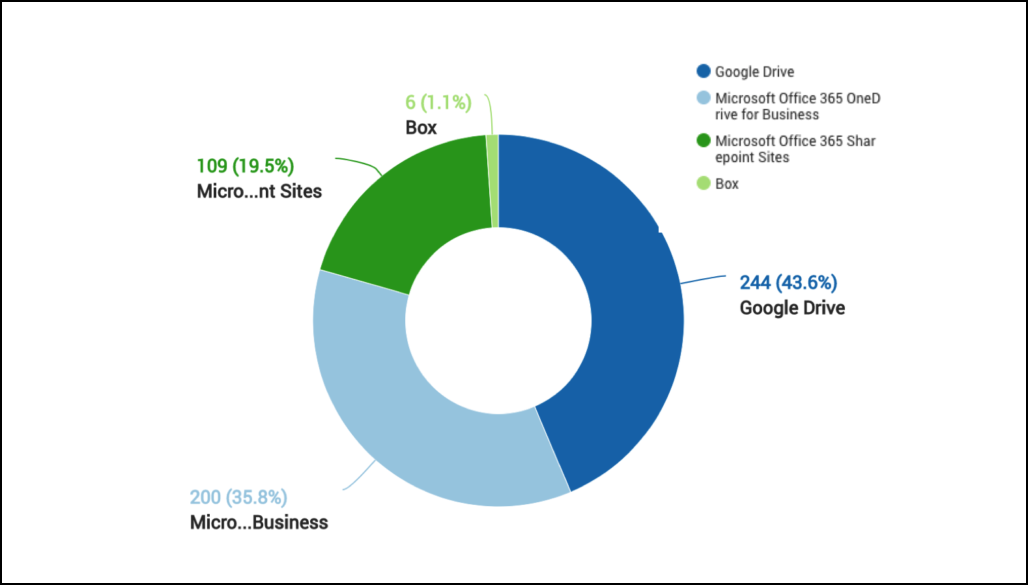
Malicious Document Analyses
A common scenario is followed by the phishing attacker in which Office file comprises embedded macros and upon clicking on it, and editing option prompts. It is observed that the Microsoft Excel file comprises of workbook_open() function. This denotes the execution of macro code when the file is opened. At the initial stage, the macro code is heavily obfuscated with a subroutines nature that comprises a lengthy variable declaration. All these functions get a call within the workbook_open(). A Visual Basic macro launches cmd window, which successively invokes PowerShell upon deobfuscation.
Now the PowerShell cmdlets start downloading the payload from an SSL site i.e., https://lambda[.]sx. This website appears like the webserver that is coded via the GO programming language. The suspicious content of the document cannot be connected with the internet server or its proprietor at this stage. We are imagining that the website is compromised for hosting malicious programming. During these campaigns, we found that the payloads are released from known cloud services and some compromised web servers.
The payload of Phishing Attacks – Pony
Already downloaded payload accomplishes the settings of unknown email theft botnet known as Fareit or Pony. This family of malware has been utilized in the phishing campaigns from the time its source code was availed for the sale in the underground hacking forums. During the analyses, laboratory experts found that the payloads were created from Pony builder 2.0. They are having the properties equal to the original samples of Pony, which can be seen wider before its code gets sold. The flow of the sample is obfuscated in a complicated manner than its predecessors. However, it uses the exact concept as that of Push-to-Ret, which recreates a call in return. By creating persistence, phishing attacks begin its functioning on the targeted system. It uses the visual basic code in the machine’s Startup directory, which will generate a copy of malware in the Roaming/App Data/User. The phishing attack tries to fetch credentials or confidential content from several associated services or system folders, respectively.
Stealing browser history and cookies from infected hosts & changing the Internet settings – both of these malicious activities are attempted by the pony information theft Trojan. The major threat exhibits a procedure injection into the explorer and then, counts the persistence process. This mechanism is done for ensuring that it executes every time the computer restarts.
How To Stay Safe From Spam And Phishing Attacks?
CloudCodes team suggests the following guidelines to fight with such threats:
- Use a suitable CASB solution to detect and fix Cyberattacks
- Enforce policy on using the unsanctioned services
- Apply data loss prevention policies at their accurate location
- Activate the “View known file extensions” feature on Windows OS
- Take backup and enable the versioning of core data in cloud apps
- Avoid using documents about which you are totally unaware
Conclusion
With the shopping sale around, enterprises and worldwide users should pay extra attention to their online activities. Draw special attention towards the platform where sharing of business content takes place. Year after year, phishing attacks or other threats are enhancing. You can take this as a warning and hence, stay vigilant for safe digital shopping.

