Cloud CRM means a customer relationship management technology where CRM tools, CRM software, and enterprise’s customer records all are placed on the cloud. All these things are availed to users worldwide with the help of the Internet. Well, where on the one hand, CRM is providing an effective platform to work, on another hand, it is also rending a rich platform for Cyberattacks to take place. A team of cloud security experts found that Cloud CRM vector is widely used to spread the Locky Ransomware attack through DDE. The term DDE stands for Dynamic Data Exchange that is a feature present in Microsoft Office.
Role of Cloud CRM in Spreading Malware
Cloud CRM allows outsiders to interact with the insiders without any restrictions. This is conducted through the exposure of Cloud CRM workflows with external partners of the organizations. This exposing activity takes place through shared workflow elements or email portals. In addition to this, the development of interlinked cloud services creates an unknown path for malicious documents. After this, these documents get successful in spreading the threat on the respective CRM platform. For example – multiple known services consolidate with online applications like Dropbox, OneDrive for Business, Box, etc., along with other collaboration services like Slack. There is no doubt in stating that these services give flexibility during the official works but, they also lead to the birth of the infection vector for a malware. A cloud threat looks for just one point to dismiss the entire platform. When this one point is encountered, malware starts its functioning by delivering malicious content to unsuspected users via Cloud CRM.
Uploading of malicious documents on the CRM platform gives birth to the presence of malware on the online storage. Not only this but, many other daily computer activities are there that permit threat to enter into the services. An employee working with insecure and unmanaged device can upload files in the form of attachments. Many industries are there in today’s market who give their vendors and external partners complete authority to work with their CRM services. A firm can control the uploading of files within an internal part but, what about the external arenas? Enterprises do not have any control over the partner or vendor systems and hence, no control over documents uploading.
Such type of miserable activities cause entering of malicious document into a rich collaborative platform. Once these documents get shared on the cloud CRM service, they are treated as part of the organization workflow that is available for all employees.
A Scary Fact – External vendors or partners will be having authority to access business confidential information because they are engaged in that particular business workflow.
Flow Structure to Spread Locky Ransomware in Cloud CRM
We will illustrate the concept of this entire blog section with an example. Suppose a file named as BusinessFinanceRecord.doc is malicious that was initially received by a victim of an enterprise. The same victim uploaded this document on the user system of Cloud CRM. Either through manual operation or automatic synchronization, malicious file gets imported into the collaborative system. This BusinessFinanceRecord.doc threat file is pernicious because it comprises of latest DDE attack for infecting vulnerable users.
Once this BusinessFinanceRecord.doc is on the Cloud CRM, all the partners and peers associated with that platform will imagine that a victim created this file and now, it is to be processed further. Tons of people who work on that collaborative platform will open this file. On the first click for file opening, the person will face 2 warning messages. The first warning indicates that file comprises of linked file.
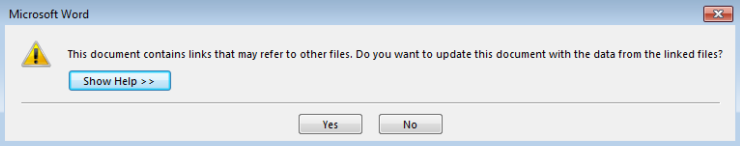
The second warning says user to begin command line programs.
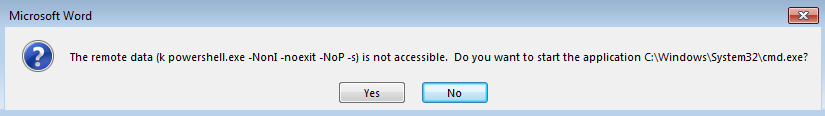
Now, the file shows a message that ‘Word is unable to obtain the content’.
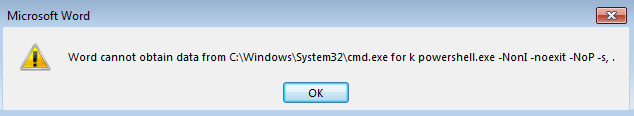
When you will click on OK button of last message prompt window, it opens a PowerShell script. This script automatically starts downloading the Locky Ransomware from attacker-controlled or compromised domain. It first downloads the information encoded with Base64 via HTTP GET request. The decoded content comprises URLs within it for downloading malicious code from the Internet. Binary code is first downloaded from any of the available domains with help of the HTTP GET request. At the %TEMP% folder as “heropad64.exe” location, downloaded executable is stored and executed. A binary callback connection is established to the command and control server for downloading the second level. This will custom the encryption for Locky Ransomware. The encrypted payload is then decrypted on the disk located at %TEMP% folder as “heropad64.exe” and then, again executed. Finally, the Locky Ransomware attack starts encrypting and, appends the file extension “.asasin” to the current victim’s document. When the encryption gets finished, it shows a warning message. This message asks the victim to pay the specified ransom to decode the file.
Conclusion
Things are not ending in today’s date, whether it is about technology or attacks. A continuous enhancement in the Locky Ransomware can be seen that is demanding to grow up cloud security for prevention. Use of DDE attack that does not require macros, is currently the latest update in the threat. This means that enterprises need to go with the latest security trends for preventing Locky Ransomware in Cloud CRM.

