In recent times organizations across the world or verticals are adopting AWS as their cloud platform and migrating their on-premise workloads to AWS. While organizations are moving, they should always remember that security on cloud platforms is a shared responsibility.
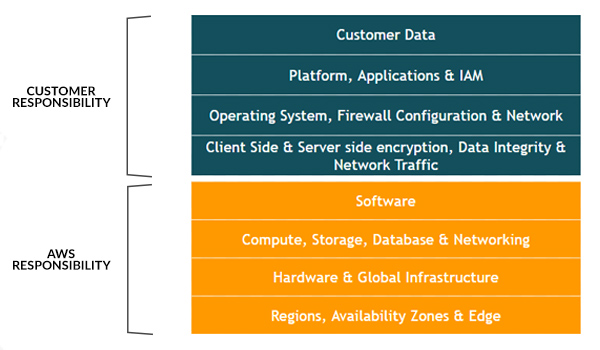
AWS Responsibility
- Protecting the AWS Infrastructure
- Includes hardware, software, and network to run the services provided by AWS
Customer Responsibility
- IAM permissions for a user accessing their account
- Managing and classifying data such as encryption
- Configuration of AWS resources
- Management of guest operating systems in case of EC2
- Managing software installed on the EC2
Center for Internet Security(CIS) has come up with best practices for various cloud platforms, including AWS.
Some of the best security practices for AWS:
- Avoid using a root account to access AWS. The root account is the most privileged. It has unrestricted access to all AWS resources.
- Mandate multi-factor authentication (MFA) for all IAM users, including root account, has access to AWS console. MFA brings additional security control.
- It is highly recommended that all credentials that have been unused in 90 or higher days be removed or deactivated.
- AWS provides Access keys; it consists of an access key ID and secret access key, used to sign programmatic requests that you make to AWS. All-access keys should be regularly rotated or change periodically. It means no hard coding of access keys in source code.
- Ensure IAM password policies follow enterprise-grade standards such as upper case, lowercase, special characters, etc.
- Remove access keys associated with the root account.
- As part of IAM policies, avoid “.” administrative privileges to IAM users. It is recommended and considered standard security advice to grant the least right—that is, allowing only the permissions required to perform a task.
- Ensure AWS CloudTrail is enabled in all regions. The recorded information includes the identity of the API caller, the time of the API call, the source IP address of the API caller, the request parameters, and the response elements returned by the AWS service. This information can be useful as part of incident response management.
- Ensure the AWS Config is enabled in all regions. The recorded information includes the configuration item (AWS resource), relationships between configuration items (AWS resources), any configuration changes between resources. It is recommended to enable AWS Config in all regions.
- VPC Flow Logs should be enabled to capture information about the IP traffic going to and from network interfaces in your VPC.
- Ensure a log metric filter and alarm exist for:
- CloudTrail Policy Changes
- IAM Policies Changes
- Usage of the root account
- Sign-in success or failures to console without MFA
- S3 bucket policies changes
- AWS Config configuration changes
- Route Table/Network ACL/VPC/Network Gateway changes
- Ensure no security groups allow ingress from 0.0.0.0/0 to port 22. Port number 22 allows remote connectivity services such as SSH.
- Ensure no security groups allow ingress from 0.0.0.0/0 to port 3389. Port number 3389 allows remote console services such as RDP.

